- I guess you are looking for this tool. Pyrit allows to create massive databases, pre-computing part of the IEEE 802.11 WPA/WPA2-PSK authentication phase in a space-time-tradeoff. Exploiting the computational power of Many-Core- and other platforms through ATI-Stream, Nvidia CUDA and OpenCL, it is currently by far the most powerful attack against one of the world's most used security-protocols.
- WPA is not LM or NTLM. What you are asking is practically impossible. You would need 2,362,609 Radeon 7970 GPUs to brute force WPA length 8 in less than 6 hours. And as brute force has exponential time complexity, you would need 570x more 7970s to brute force length 9.
- Engine) for WPA cracking and evaluate whether the WPA encryption is strong enough and o ers enough security. Therefore it is tried to crack WPA by using brute force password cracking method, because it is the only known way to crack WPA 23 (WPA cracking is investigated in next chapter). A brute force password cracking is generally.
Here we will automatically select best suited wordlists and keyspaces to maximize your chances to win the lottery. Advanced WPA search usually takes 1-3 hours therefore it is paid option. The price of running Advanced WPA search is 0.005BTC and of course you will get your password for free in case of success.
Cracking Wpa Wpa2 Psk
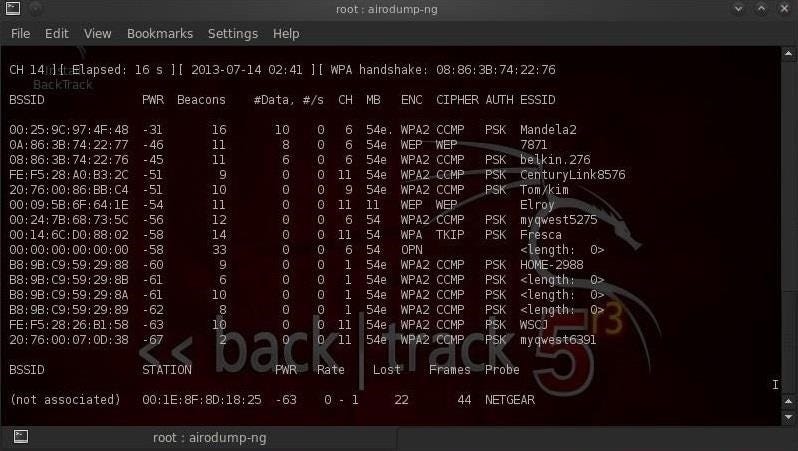
Best Gpu For Wpa Cracking Free Fire

09-01-2017, 05:48 PM (This post was last modified: 09-01-2017, 06:08 PM by roundcube222.)
Wpa Cracking Tool
For WPA/WPA2 hash crack, There are three major types of attacks (Dictionary & Rule-based & Mask) attacks.
I was testing what is the fastest attack and i found out that the Dictionary is the slowest one then the other two types. The Rule-based and Mask attack gave me nearly the same speed.
Is it true that the Mask attack is faster than the the dictionary attack ?
1- My first question is that i understand for mask attack , that the passwords are generated to by the CPU , then it is copied via the PCI express to the GPU, then the GPU start working on the hashcrack. is this correct ? i give example below to the command i use to performe mask attack
hashcat -m 2500 hash.hccapx -a3 -?d?d?d?d?d?d?d?d -w3
So if this is correct why mask attack is much faster than dictionary attack, although both copy the data from CPU to GPU through the PCI express ? in my testing i found out that always the mask attach is faster than dictionary attack.
2- I think that the fastest attack is the Rule-based, because it modify the wordlist inside the GPU so copying is no longer need from CPU to GPU. but to my surprise that i found that some times the mask attack is faster than the Rule-based attack, although the mask attack should be slower because it copy the generated words from CPU to GPU which takes alot of time... i though that Rule-based attack should be faster because all the work is done inside the GPU in terms of modifying the wordlist to many other words.
3-Does the wordlist size have effect on the GPU cracking speed incase of Dictionary attack ? or Rule-based attack? or mask attack ? i think that the bigger size of the wordlist , the more GPU faster speed the rule-based attack will be .. is this correct ? i also noticed that the crack speed decrease incase of bigger size of wordlist for the dictionary attack ? so it is opposite to Rule attack in this case.... and also what about mask attack, does the longer size of mask attack cause speed difference?
4-If we are going to make a sorting from fastest to slowest methods for cracking WPA, would it be
1- Rule based attack
2- Mask based attack
3-Diectionary attack ?
Thank you.
Michael Robert
I was testing what is the fastest attack and i found out that the Dictionary is the slowest one then the other two types. The Rule-based and Mask attack gave me nearly the same speed.
Is it true that the Mask attack is faster than the the dictionary attack ?
1- My first question is that i understand for mask attack , that the passwords are generated to by the CPU , then it is copied via the PCI express to the GPU, then the GPU start working on the hashcrack. is this correct ? i give example below to the command i use to performe mask attack
hashcat -m 2500 hash.hccapx -a3 -?d?d?d?d?d?d?d?d -w3
So if this is correct why mask attack is much faster than dictionary attack, although both copy the data from CPU to GPU through the PCI express ? in my testing i found out that always the mask attach is faster than dictionary attack.
2- I think that the fastest attack is the Rule-based, because it modify the wordlist inside the GPU so copying is no longer need from CPU to GPU. but to my surprise that i found that some times the mask attack is faster than the Rule-based attack, although the mask attack should be slower because it copy the generated words from CPU to GPU which takes alot of time... i though that Rule-based attack should be faster because all the work is done inside the GPU in terms of modifying the wordlist to many other words.
3-Does the wordlist size have effect on the GPU cracking speed incase of Dictionary attack ? or Rule-based attack? or mask attack ? i think that the bigger size of the wordlist , the more GPU faster speed the rule-based attack will be .. is this correct ? i also noticed that the crack speed decrease incase of bigger size of wordlist for the dictionary attack ? so it is opposite to Rule attack in this case.... and also what about mask attack, does the longer size of mask attack cause speed difference?
4-If we are going to make a sorting from fastest to slowest methods for cracking WPA, would it be
1- Rule based attack
2- Mask based attack
3-Diectionary attack ?
Thank you.
Michael Robert